

Jetspeed provides several administrative portlets to manage users, groups, roles and permissions. To see them, logon with the username/password = admin/jetspeed. Click on the Security menu item, and should see something like this:
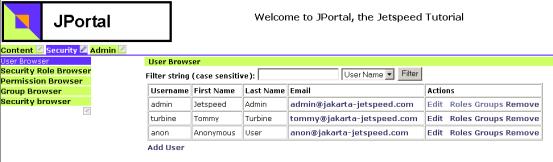
The User Browser allows you to add/edit/delete users, and associate relationships between users-groups and user-roles. The other browsers provide add/edit/delete maintenance for roles, groups and permissions.
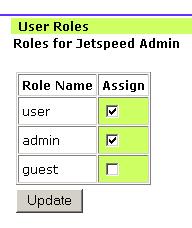
The user/group association isnt used specifically by the default security system. User/role associations are used throughout the system to perform role-based security checks. A security constraint in Jetspeed is defined between a role and a resource for a given action (permission). In this example from a security registry, we are declaring a role-based declarative security constraint called requires-accountManager.
<security-entry name="requires-accountManager">
<meta-info>
<title>Account Manager</title>
<description>Grant full access to Account Manager Role, read
access to Support Role.</description>
</meta-info>
<access action="*">
<allow-if role="accountManager"/>
<allow-if role="admin"/>
</access>
<access action="view">
<allow-if role="guest"/>
</access>
</security-entry>
We are granting full access to users with the role accountManager or admin for all actions(permissions), but only granting view access to users with the role guest. All other users are denied access to the resource protected by this constraint.
We will look at how to associate a security registry entry with a portal resource in the section after next.