

Jetspeed 2 security architecture provides a comprehensive suite of security services that can be used to protect a wide ranging type of portal resources. The security service implementation is fairly independent of the other portal services and can be reused outside of the portal application. At its core, Jetspeed 2 security services rely entirely on JAAS to provide authentication and authorization services to the portal:
Both authentication and authorization services have been implemented with the goal of providing a direct plugin to the underlying application server security framework. Jetspeed 2 can leverage the underlying application server login module as well as through the use of JACC, the application server policy management capabilities available in J2EE 1.4 (see API Specifications ).
JAAS defines the contract for authentication and authorization but does not specify any guidelines for the management of the security resources. Jetspeed 2 provide a modular set of components aims at providing management functionality for the portal security components.
Leveraging Jetspeed 2 component, architecture, the security services provide a set of loosely coupled components providing specialized services:
Jetspeed 2 security components are assembled using Dependency Injection . By default, Jetspeed uses the Spring Framework as its default IoC container.
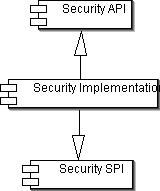 Jetspeed 2 security services are founded on a set of modular and extensible security modules exposed through an SPI model. The SPI model
provides the ability to modify the behavior of the Jetspeed coarsed security services (UserManager, RoleManager, GroupManager)
through the modification and configuration of specialized handlers. For
instance, Jetspeed security services can be configured to retrieve user security principals through the default Jetspeed store or through an
LDAP store or both.
Jetspeed 2 security services are founded on a set of modular and extensible security modules exposed through an SPI model. The SPI model
provides the ability to modify the behavior of the Jetspeed coarsed security services (UserManager, RoleManager, GroupManager)
through the modification and configuration of specialized handlers. For
instance, Jetspeed security services can be configured to retrieve user security principals through the default Jetspeed store or through an
LDAP store or both.
A
SecurityProvider
exposes the configured SPI handlers to the security services. Jetspeed component assembly (based on Spring) architecture provides an easy way to
reconfigure the security services to satisfy the needs of a specific implementation.
Role based access control (RBAC) in Jetspeed 2 support multiple hierarchy resolution strategies as defined in The Uses of Hierarchy in Access Control . See Hierarchy Management Overview for more information.