With the Jetspeed DefaultCredentialHandler special management of password credentials can
easily be configured. Through the provided
PasswordCredentialProvider and
InternalPasswordCredentialInterceptor components custom logic can be plugged in for:
PasswordCredential implementationCredentialPasswordEncoder is available from the
PasswordCredentialProvider passwords will be encoded with it before they are persisted.
The provided
MessageDigestCredentialPasswordEncoder uses
MessageDigest hash algorithms for the password encryption, and can for example be
configured to use SHA-1 and Base64.
CredentialPasswordValidator is available from the
PasswordCredentialProvider, passwords will be validated with it before they are persisted.
The
DefaultCredentialPasswordValidator for example enforces non-emtpy password. And
with the
SimpleCredentialPasswordValidator a minimum length and a minum number of numeric
characters can be enforced.
InternalCredential lifecycle eventsDefaultCredentialHandler is provided with an
InternalPasswordCredentialInterceptor, it will invoke this interceptor (or an arbirary
set if
InternalPasswordCredentialInterceptorsProxy is used) on:
ValidatePasswordOnLoadInterceptorCredentialPasswordValidator
of the PasswordCredentialProvider, the same as used when a password is changed.
EncodePasswordOnFirstLoadInterceptorCredentialPasswordEncoder from the PasswordCredentialProviderPasswordExpirationInterceptorexpiration_date and is_expired members of the
InternalCredential and sets the expired flag when on authentication of a user
its (valid) password is expired. The authentication will then fail.PasswordCredentialValveImpl can be
used to request or even enforce users to change their password in time to prevent a password
expiration (described further below).
MaxPasswordAuthenticationFailuresInterceptorDefaultCredentialHandler.
PasswordHistoryInterceptorPasswordAlreadyUsedException will be
thrown. But setting a new password through the administrative interface still allows any
password (when otherwise valid) to be set.
The DefaultCredentialHandler only supports one interceptor to be configured.
But, with the
InternalPasswordCredentialInterceptorsProxy, a list of interceptors can
be configured which then will be invoked sequentially.
Jetspeed comes out of the box with several of these interceptors configured, and its very easy to change and extend.See the security-spi-atn.xml section in the Security Services Configuration document for a description of the default configuration. Also provided there is an example how to setup the interceptors to restore the "old" (and much more restrict) configuration provided with the 2.0-M3 release and earlier.
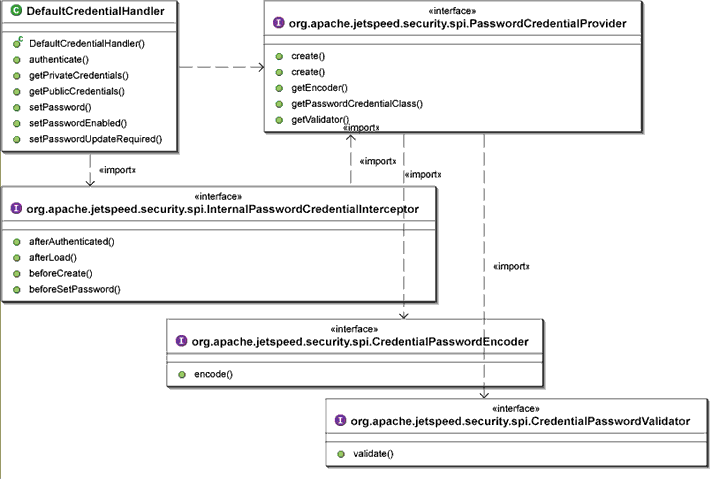
The class diagram below describes the components used for the
DefaultCredentialHandler
implementation.
The OJB mappings for the default credentials implementation are described in
security_repository.xml:
InternalCredential: Maps to the SECURITY_CREDENTIAL table.